Last time, we gave you a crash course to get you acquainted with UFW. We covered how to enable, disabled and delete rules. We also made sure you know the importance of preserving an SSH connection in a production environment. If you missed out on this blog, please check it out here. As I will try to keep the material fresh and not repeat myself too much. For the seasoned among us, this is for you! We will explain default rule states, how using service names can save you time, good ways to manage a multitude of rules, working with logs, and how to automate parts of the rule making process using some good old scripting. Not to forget some details about UFW options.
At this point, we will get out a VM to work with. To do this, you can spin up a server distribution of your choice using Virtualbox. I like Virtualbox because it is easy to install and use. It works for Linux, Mac or even the dreaded Windows user. Anyone can try this out, in other words. I would love to talk more about Virtualbox, but then we would be beyond the scope of this blog.
DEFAULT RULES
First, we will want to check the status of UFW.
sudo ufw status
You can see that UFW is inactive by default. So we will want to go ahead and activate that right now.
sudo ufw enable
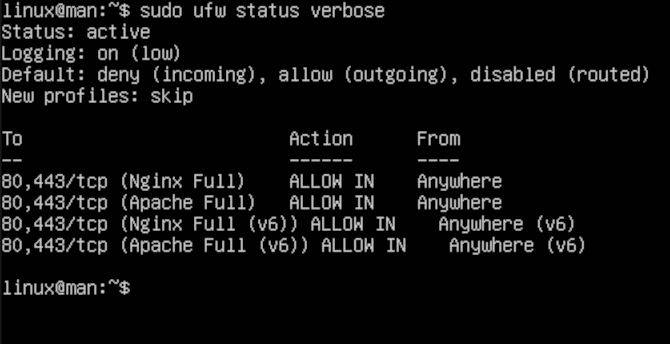
We can check out the status again using verbose. This way, we will see a detailed readout of what UFW does by default.
sudo ufw status verbose
As you can see in the readout, we have some default rules that are great for your laptop or PC. As you can see, it says,” Default: deny (incoming), allow (outgoing), deny (routed).” But today we are talking about servers.
SERVICE NAMES
We will show how to use it with Nginx and Apache to demonstrate some customization you might need for a web server. Please make sure to install one or both of these applications to follow along. We will surely cover installation of both servers in the future, as they are a gateway to many projects based in the Linux ecosystem.
sudo ufw allow "Nginx Full"
sudo ufw allow "Apache Full"
Now, you can see, it is that simple to get your server running on the correct ports. As well as with the right protocols, just using service names. Next, we can check on the applications UFW has listed as a result.
sudo ufw app list
TIPS & TRICKS
Next, let us say that you are managing a server that has a ton of rules on it. The rules that you need to see are at the very end. You can use tail to help you see the last 10 or the last 100, you decide the number.
sudo ufw status numbered | tail -10
Similarly, you might want to be able to scroll up and down to see the rules on a smaller screen or just for convenience. We will use less at the end to make things more manageable.
sudo ufw status numbered | less
To exit the list.
:q
You may find yourself wondering, can I just block an IP on the network. Of course, with one swift keystroke.
sudo ufw deny in on eth0 from 0.0.0.0
Please note, 0.0.0.0 is in place of an IP you wish to deny on an Ethernet connection. Finally, you might also want to check on your logs just to see what is going on. To troubleshoot or just to see if someone is knocking around where they should not be. It is more useful than you may know to have access to your logs. The commands provide two different ways to see the same data. You could attach this to a cron job to automate this and print it into a file for you. You guessed it, we will have another blog to demonstrate cron jobs.
sudo cat /var/log/ufw.log | less
sudo tail -f /var/log/ufw.log
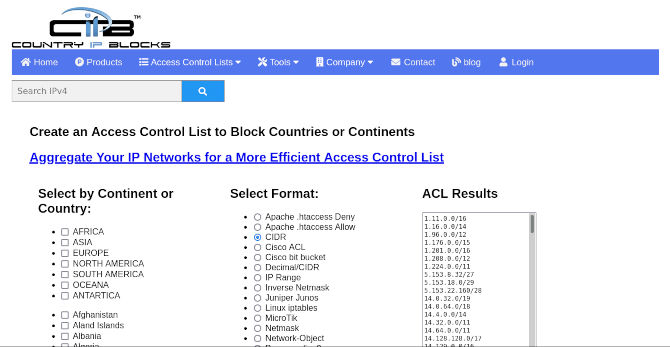
Now, this next part is for those that need to take down a lot of IP. You will need a site to help you make a list for a country, for example. We will use countryipblocks to source our list. Make sure that you select CIDR along with the desired country. Copy it into a text file. Name it something to help you remember what it is like, cidr-list.txt. Let’s say Russia is having a good time with you. You would be there for days trying to block them all by hand, one by one. We are here to help! This can still take a few hours or even the better part of a day. So only do this step if you have time or really need it.
cat cidr-list.txt | grep -v ^# | while read subnet; do sudo ufw deny from $subnet; done
This code deserves some explanation. The first part uses cat to print cidr-list.txt. The next part uses grep to read the list. Then after that, our script then uses subnet as a value to store the list. Last, we will run a UFW command using that value to then represent the list. Note that you can use other terms besides deny. You can allow an entire office complex, so that they can access, for a more enterprise use.
OPTIONS
I will provide the terms and explanation below for UFW options.
sudo ufw --version
Version number and exit.
sudo ufw --help
Help message that details command options like this and exit.
sudo ufw enable
Enables firewall.
sudo ufw disable
Disables firewall.
sudo ufw reload
Reloads firewall.
sudo ufw default allow outgoing
sudo ufw default deny incoming
sudo ufw default reject incoming
Default policy for traffic direction, where direction is one of incoming or outgoing.
sudo ufw logging on
sudo ufw logging off
Logged packets use the LOG_KERN syslog. Specifying the on or off for the specified log level. The default log level is ’low’.
sudo ufw reset
Disables and resets firewall to installation defaults.
sudo ufw status
Show status of firewall and UFW managed rules.
sudo ufw show <argument>
Display information about the running firewall.
sudo ufw allow <argument>
Add allow rule.
sudo ufw deny <argument>
Add deny rule.
sudo ufw reject <argument>
Add reject rule.
sudo ufw limit <argument>
Add limit rule.
sudo ufw delete <argument>
Deletes the corresponding rule number you specify.
sudo ufw insert <argument>
Inserts the corresponding rule number you specify.
Please note, <argument> is in place of a rule, IP, port number, or service name. Knowing the options for UFW will save you so much time going forward. You can use other methods to block IPs. We will go over many more useful tools to help you harden your server further. I look forward to writing about all the different types of server hardening, free and open source software made for Linux. Till then, thanks for reading.