You may have heard of UFW, which is commonly found on Debian systems. Today we bring you Firewalld, which is commonly found on RHEL systems, as it was created by RHEL software engineers by the name of Eric Garver, and Thomas Woerner. Firewalld is yet another wonderful piece of technology built in Python. All the wonderful toys built on Python. We will be checking it out on Fedora server addition using Virt-manager, another RHEL creation made in Python.
Firewalld is a zone-based system that monitors traffic and take actions based on a set of predefined rules applied against incoming and outgoing packets. This is an approach that RHEL introduced in version 7.0 back in 2011 when bringing Firewalld into the fold. Today we will go over the basic for zones and services. Next, we will cover how to allow or deny by service. Finally, we will then go over how to allow or deny by ports and in particular UDP. This should give you a good enough understating in which to start identifying your own uses. Let’s get right into it!
Basics
You may notice that Firewalld is running by default on many RHEL-based distributions. So if you are running Rocky, CentOS, or Fedora server addition you only need to change the configuration as you see fit. For testing, we will be running in root, be sure to use sudo if you are not going to run in root. Why don’t we look and see what the zones are listed?
firewall-cmd --get-zones
Now you can see that we have numerous zones going on here. They are all slightly different depending on your system. Sometimes a distribution will be listed, perhaps libvirt or even nm-shared like in our case. This depends on the distribution you are running, whether you are using a VM or not. We are using Virt-manager, so this changes our zones. The zones to notice are as follows.
- block
- dmz
- drop
- external
- home
- internal
- public
- trusted
- work
Now we can go ahead and use a generic command that will pull up your default zone.
firewall-cmd --list-all
Now as you can see, our server name is mentioned as active. The target is listed as default, which also happens to be the public zone, with all the services listed as follows.
- cockpit
- dhcpv6-client
- ssh
The services may differ as well for similar reasons as the zones might. If you are testing in a virtual machine like us, you will see something similar. If you’re on your own server, you may see something very different. The point is you can enable services or disable them as you need to.
Add & Remove Services
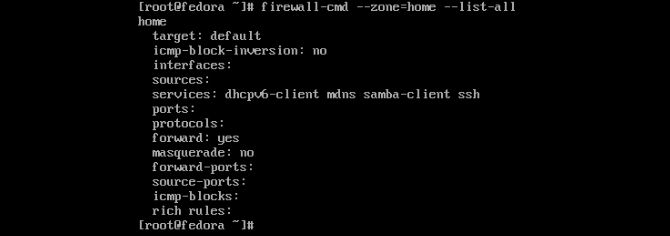
You may have some services you don’t want running. As a Linux user, my goals are always to do everything with as little system as one might need. The philosophy of firewall use is to only use what you require, in terms of in bound connections. So, why don’t we take our list and remove something? We should check on a zone by the name of home. Let’s see what services it contains.
firewall-cmd --zone=home --list-all
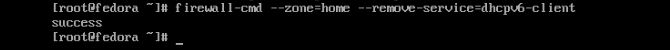
Now you can see we have a dhcpv6-client running. Depending on your needs, you may as well be rid of it. If you know you are not running that protocol, then you can remove it like so.
firewall-cmd --zone=home --remove-service=dhcpv6-client
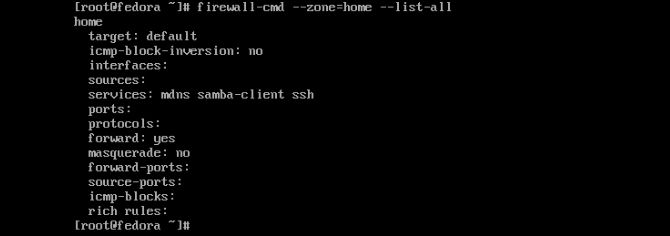
Now we can check on our services to see whether it is still running or not.
firewall-cmd --zone=home --list-all
Now that you know how to remove a service from a zone. Let’s add a new one to the very same zone to help us with a theoretical problem. Let’s say you locked yourself out of a much-needed Samba share, and you just need a file to help you fix it. The file is on your server, which you prefer visual access to. We can add something like FTP (File Transfer Protocol) to help grab the needed document.
firewall-cmd --zone=home --add-service=ftp
Now you can retrieve your file to fix Samba and remove FTP later if you wish. Adding and removing services applies to other zones as well. You just need to make sure you know what they do before you go removing something you need, as you may need to add the service back. The great thing is, as long as you have access, you can add it again.
Add & Remove Port Access
Now another way to use Firewalld is by specifying port numbers. Furthermore, we may need to add a particular protocol to this port. Maybe you are just wanting to use a firewall as intended. You can close unused ports similar to before, yet using the numbers instead. First let’s check out the external zone.
firewall-cmd --zone=external --list-all
Notice the only thing we see enabled is SSH as a service. Why don’t we add a few ports we think we might need for an application we want to develop that needs UDP enabled specifically? Let’s open the port like so.
firewall-cmd --zone=external --add-port=5644/udp
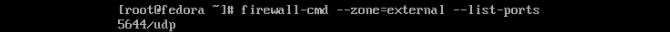
Now we can check on that to make sure we got the results we intended. Similar to –list-all we will use –list-ports instead.
firewall-cmd --zone=external --list-ports
Now you can see we have started the prep to have the access we need for our genius application. Let’s say we decided we need to use another port because this one was discovered by an unwelcome visitor. We can remove the specified we just did like this.
firewall-cmd --zone=external --remove-port=5644/udp
Now we can quickly assign our port to another random number. Make sure always to check and see what is running on your ports on a production environment before assuming that you can just pick a port. You might run into different results than you would like.
firewall-cmd --zone=external --add-port=8846/udp
Now you can continue testing your application on a new port. You can also use some other software to mitigate port knocking. But that is not in the scope of this blog. Now you can assign zone services and give port numbers access along with what protocol they need. Giving you a fair command over Firewalld. Remember to always block everything you don’t need. Make sure to research services running by default before you remove them. Also, you will want to make sure your ports are not open if need be. No reason to leave anything open that does not need to be used for something like SSH. In fact, changing your SSH over to a port would be a nice way to get off the defaults. Thanks for reading.